Role-Based Access
Ensure your data is in the right hands.

Data Security Done Right
With customizable user roles, precise access control lists, tailored data visibility settings, and comprehensive audit logs, you can manage information visibility while keeping your business secure.
- Document Management
- Candidate Sourcing
- Interview Scheduling
- Offer Management
User Role Customization
Define specific roles and responsibilities for each team member, ensuring that everyone has access to the tools and information they need without compromising security.
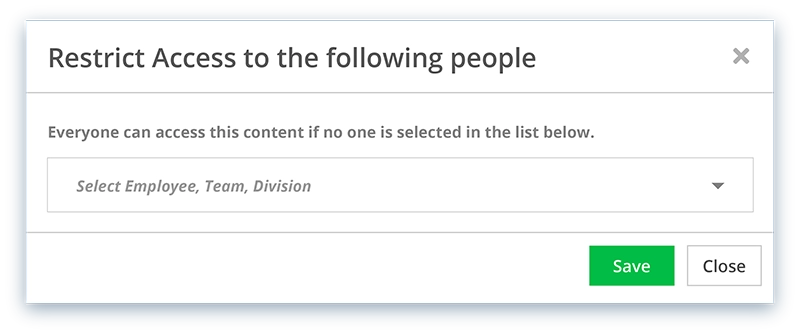
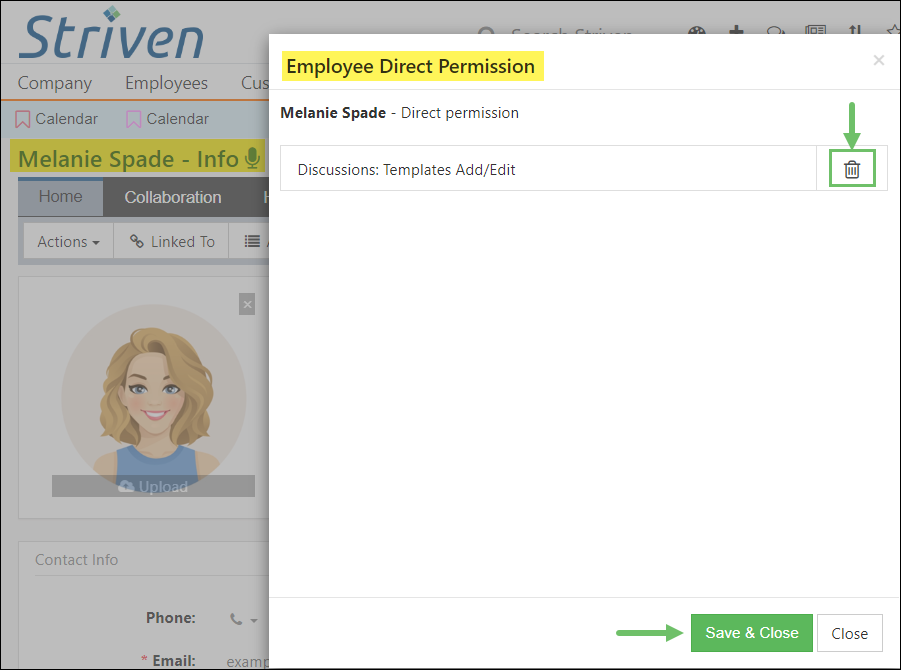
Access Control Lists (ACLs)
Grant or restrict access to specific features and data within Striven, allowing you to maintain consistent control over sensitive information and ensure compliance with company best practices.
Data Visibility Settings
Customize data accessibility to match your organizational needs, ensuring that users can only view the information relevant to their role, enhancing both security and efficiency.

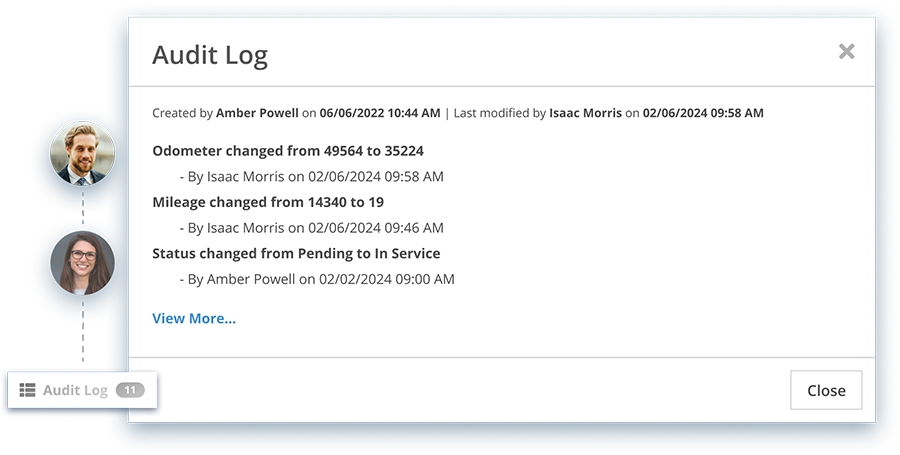
Audit Logs
Keep track of all user activities with detailed audit logs. Provide a clear and traceable record of who is creating, accessing, copying, and making status updates within the system.

“Striven has been, by far, the best ERP software I’ve used in 25+ years.”
—Darin B., G2 Review
Ready to try it? Start here.
Frequently Asked Questions
-
How does user role customization benefit my organization?
+
User role customization allows you to define specific permissions and responsibilities for each team member, granting access to the tools and data they need without exposing sensitive information.
-
What are Access Control Lists (ACLs) and how do they work in Striven?
+
Access control lists grant or restrict access to specific areas within Striven, giving you granular control over who can see and do what within the system.
-
Can I customize what each user can see in Striven?
+
Yes, with data visibility settings, you can tailor data access to ensure users only see information relevant to their roles, enhancing security and operational efficiency.
-
How do Audit Logs enhance security in Striven?
+
Audit logs provide a detailed record of all user activities, making it easy to track changes and access, maintaining security.
-
How easy is it to set up User Role Customization in Striven?
+
Striven makes it straightforward to set up user role customization with an intuitive interface that allows you to define roles and permissions quickly and easily.
-
What happens if an unauthorized user tries to access restricted data?
+
Striven’s access control lists and data visibility settings keep unauthorized users from accessing restricted data.
-
Can I get reports on user activity within Striven?
+
Yes, Striven’s audit logs provide comprehensive, time-stamped reports on user activities, allowing you to monitor access and changes made within the system.
-
How does Striven ensure that only authorized personnel access sensitive data?
+
Striven ensures this through a combination of user role customization, access control lists, and data visibility settings, all backed by detailed audit logs to monitor and verify access.
Striven's Got You Covered
Whatever your business, Striven is here for you, making your supply chain management a breeze.
