Cloud networks are the wave of the future. The ability to access your business assets anywhere is attractive to many companies—especially those with a remote team. However, protecting digital assets requires sophisticated knowledge and foresight.
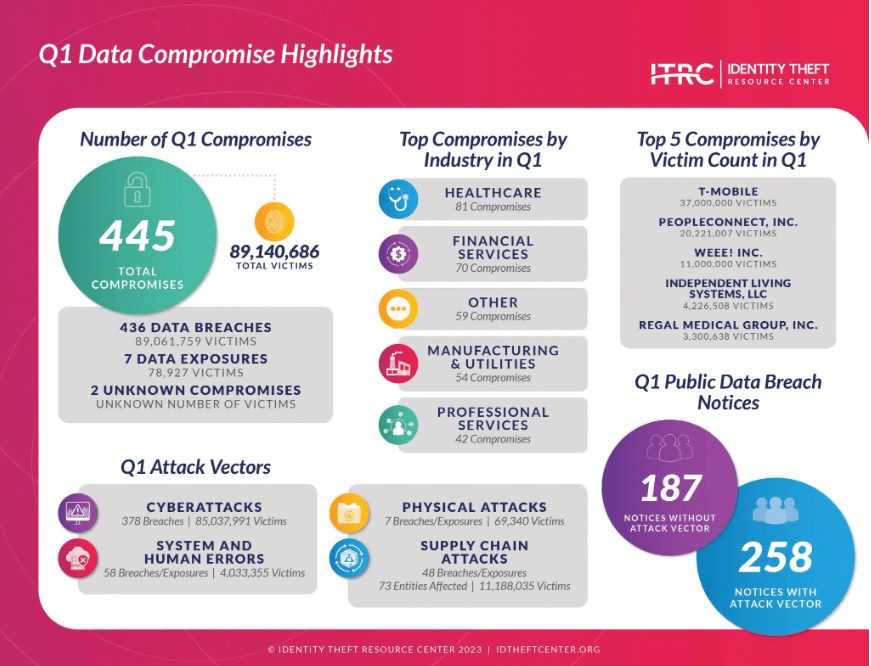
The cloud services market is a $266.4 billion industry and growing yearly. As with anything online, though, cybercriminals will try to find ways to access personal information or take systems down. Protecting your business’s assets is a vital step in ensuring your customer and business data stays safe.
Cloud security is often a concern of small-business owners. Some may even shy away from cloud computing due to fears of exposing trade secrets or customer lists. That said, you can take steps to protect your business’s assets while reaping the benefits.
1. Choose the Right Provider
Your first step should involve choosing your cloud provider wisely. What steps do they take to ensure secure digital assets? Top cloud-based hosting companies have the best security software imaginable. Because they represent numerous clients, they can invest more in world-class protection.
Ask how they back up information. What happens if a hack does occur? Find out how frequently they update their security systems and what they do to identify and quarantine potential threats.
2. Match Specialties
Some cloud providers specialize in working with particular industries. A company that already has clients in your sector better understands your specific security needs. Cloud migration can take endless hours of moving databases to a new setup. It helps to know which system you want and why.
Find a provider willing to move information over for you in a secure environment so you start the process with less risk.
3. Secure Your Wi-Fi

It doesn’t matter who your provider is if the devices used to access data are compromised. Make sure company Wi-Fi is secure so that non-authorized people can’t log in and watch what your employees are doing. Instead, set up a guest Wi-Fi if you want to provide convenient Wi-Fi connectivity to on-premises visitors.
The Covid-19 pandemic showed us that remote work environments are effective. Your IT department should pay particular attention to security concerns for employees working off-premises. If remote staff needs to access information from the main office, set up a secure VPN network that’s resistant to cyber-attacks.
4. Require Regular Password Resets
Require your workers to reset their passwords for logging into the office network every 45 days or so. Set complexity rules around the types they can create, don’t allow repeated passwords, and ask them to protect their current login information. Multi-factor authentication, where users receive a secondary verification code on a trusted mobile phone, is a must.
Although not as common as some other attack vectors, there have been occasions when someone works at a coffee shop and a nearby table notes their login and steals it to access a company website.
5. Security
Just because news of corporate data compromise no longer dominates the headlines, breaches are still happening. Most in-house IT staff are well-versed in a number of disciplines, but effective data security practices are a moving target.
Consider hiring a 3rd-party cybersecurity expert. The level of creativity and malice of today’s data theft actors is astonishing and they only need to succeed one time. To avoid catastrophe, your security needs to be right every time.
Today’s outsourced cybersecurity firms offer surprisingly inexpensive services to help businesses stop attacks before they occur.
6. Train Employees
One of the top things you can do is train your employees in cybersecurity. Explain spoofing and phishing and how they can avoid it. Set policies to never request password information in an email.
Spend time refreshing your staff about how to keep data secure every so often. They should be very careful when working in public locations.

Should you need to terminate an employee, make sure their account credentials are disabled immediately. Otherwise, you open your brand up to vengeance attacks.
7. Keep Backups
Even if the cloud hosting company you use keeps regular backups, and most do, make sure you keep them as well. In the case of a severe cyberattack, your entire system, website, and online presence may go down.
The best way to get back online fast and avoid revenue loss is with a recent backup. However, it might take days to restore everything if you don’t. Develop a business continuity and disaster recovery plan before a catastrophe happens. In a worst-case scenario, you risk losing some data forever.
8. Keep Sensitive Data Offline
If your company has some truly sensitive data because you work with patients or the government, consider keeping some things off the internet. No matter how much software you install or how robust your security is, there’s always a chance of hacking.
If something is extremely sensitive, you can code it and use that for your online entries or just take that information to your private servers. However, they must also be kept secure.
9. Encrypt at the File Level
Even if your cloud provider uses encryption, add another layer of protection by encrypting before you upload your files. You’ll need something your remote workers can access, but it’s crucial to take that one added step to prevent sensitive data leaks.
Use database sharding to break up sections and store them in different locations to further protect documents. They may breach your network, but they aren’t likely to find the full information they need to steal private information. They’ll only have bits and pieces.
Business Cloud Security
The rate of cyberattacks has grown in the past year. More people are online, and businesses have to be remote-work-friendly. Cybercriminals are taking advantage of this, but you can stop them in their tracks—and protect business assets on the cloud—by following a few of the tips mentioned above.
Think about the different ways you might open yourself up to an attack and take steps to stop it before it happens. Your cloud provider can help by putting protections in place, and you can ramp up security on your end, too.